The World’s Biggest Threat: Cyber Warfare
Dear Readers,
Imagine losing everything.
You get out of bed, you go for breakfast, you pay for it with your credit card, and your card is declined. You call your credit card company and they tell you that your account doesn’t exist.
You’re confused, but you have to at least settle your bill before you settle your credit card issue.
You walk over to the bank to withdraw cash for your meal. You get to the ATM, type in your PIN, attempt to withdraw your money, but your transaction is declined.
Your bank account balance shows zero.
You call your bank. They have no record of who you are.
You call the government. They have no record of who you are.
You don’t exist.
This nightmare may sound like it came straight from the pages of a Tom Clancy thriller, but it could happen to you.
And it could happen to you tomorrow.
The Age of Cyber Warfare
A year ago, after the Snowden leaks, I spoke urgently about the increasing role of cyber security (which, of course, meant that cyber security stocks would climb.*)
(*There is even a new cyber security ETF now listed on the NYSE under the symbol HACK; it, too, is continuing to climb to a new 52-week high.)
Since that time, we have witnessed numerous cyber security attacks. From N. Korea’s supposed hack of Sony, to China’s potential role in the hacking of healthcare giant, Anthem Inc., the stream of major hacks around the world has now turned into a system of complex rivers.
Be warned: this is just the beginning.
The new wars of our generation are increasingly being fought with technology; from unmanned drones, to viruses that attack a nation’s power source.
While the threat of cyber warfare started many years ago, it became much more apparent in 2010, when the world discovered that Iran’s uranium-enrichment facility at Natanz was infected with a computer worm called Stuxnet.
Stuxnet succeeded in slowing Iran’s uranium enrichment by manipulating valves on centrifuges to increase the pressure inside them, damaging devices, as well as the enrichment process. This was a virus that caused actual physical damage.
The damage done to the systems were grand, but more importantly, it was done without shooting a gun, or dropping a bomb. It was done without any sort of physical infiltration.
Those who created and implemented the virus were able to destroy critical systems, all the while avoiding public and political scrutiny because evidence of its source could only be assumed, and not proven.
First Strike
The obvious culprit in Stuxnet was likely a group that wanted to hinder Iran and its nuclear programs. This would mean that the immediate finger pointing would have been directed at Israel and the U.S.
Of course, both nations would deny the attacks.
Years later, NSA whistleblower Edward Snowden would reveal that Stuxnet was created as part of a joint operation between the Israelis and the NSA’s Foreign Affairs Directorate (FAD).
Later, other officials would concur.
Via The Register:
“An unnamed US official also said that Stuxnet was part of a program called Operation Olympic Games, started under President Bush and continued under the current administration, aimed at slowing down the Iranian nuclear effort without having to resort to risky airstrikes.
General James Cartwright, a former vice-chairman of the Joint Chiefs of Staff, is currently under investigation by the US government for allegedly leaking details of Operation Olympic Games.”
Stuxnet was just the beginning of many highly sophisticated viruses that would be used to infiltrate systems of governments and private organizations.
In the years following the discovery of Stuxnet, more sophisticated versions of the virus would spring up in the Middle East. These included Flame, Duqu, and Gauss – all with the ability to steal information by activating computer microphones and cameras, log keyboard strokes, take screen shots, extract geo-location data from images, and send and receive commands and data through Bluetooth.
Some of these viruses attacked private oil companies in the Middle East, while others attacked financial institutions – wreaking havoc on oil and gas systems, and stealing everything from login data, to banking information.
But the invasions of viruses that attack systems were just the beginning.
In a recent report by Kaspersky Lab, a Russian-based security software maker that has exposed numerous Western-originated cyber-espionage operations, revealed that there could be a much bigger spying infiltration operation than ever before – one that has been happening since 2001.
Via Reuters:
“The U.S. National Security Agency has figured out how to hide spying software deep within hard drives made by Western Digital, Seagate, Toshiba and other top manufacturers, giving the agency the means to eavesdrop on the majority of the world’s computers, according to cyber researchers and former operatives.
… Kaspersky said it found personal computers in 30 countries infected with one or more of the spying programs, with the most infections seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria. The targets included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists, Kaspersky said.
…The firm declined to publicly name the country behind the spying campaign, but said it was closely linked to Stuxnet, the NSA-led cyber weapon that was used to attack Iran’s uranium enrichment facility. The NSA is the agency responsible for gathering electronic intelligence on behalf of the United States.
…Kaspersky published the technical details of its research on Monday, which should help infected institutions detect the spying programs, some of which trace back as far as 2001.”
If what Kaspersky said is true, it would mean that the program could give the NSA, or “whoever” involved, direct access to the world’s computers – even when offline.
I have over five hard drives from the manufacturers mentioned above.
How many do you have?
CLICK HERE to Share Your Thoughts on Cyber Warfare
Cyber Warfare Retaliation
While Stuxnet and its cousins were the collaboration of highly sophisticated personnel with a massive treasure chest to fund such an advanced attack, the reality is that cyber warfare is a game that can be played by anyone.
You don’t have to have billions of dollars for an army. You don’t have to have nuclear capabilities. You don’t have to have a military presence. You just have to be really smart.
With the awakening of Stuxnet, the intensity of cyber warfare has grown to all corners of the globe, and is being played by nations all around the world – including America’s enemies.
Since evidence points to U.S. responsibility for the launch of these viruses, you can bet their enemies will retaliate.
And they have.
On August 15, 2012, the eve of a Muslim holy day called Lailat al Qadr, “the Night of Power,” the world’s largest oil company, Saudi Aramco, was attacked.
Islamic hackers, who called themselves the Cutting Sword of Justice, initiated a bug that would wipe the hard drives of 30,000 Aramco personal computers, leaving only a calling card behind: the image of an American flag on fire.
Shortly after, a barrage of cyber-attacks against American interests began. Some of these included attacks on the New York Stock Exchange and financial institutions, including some of the United State’s biggest banks such as JPMorgan, CitiGroup, Wells Fargo, and HSBC. While no money was stolen, the threat was real: Hackers were able to infiltrate even our most secure systems.
Let’s not forget the hack attack I talked about in my Letter, Shocking Truths About Trading, whereby the hacking of the Associated Press’s Twitter account caused the Dow to drop 150 points-the equivalent of $136 billion in value-within a matter of minutes.
Let’s also not forget the shutdown at Nasdaq in 2013, when the system was closed for 3 hours due to a glitch in the software.
Via NYTimes:
“… (A) series of attempts by a market operated by the NYSE Euronext to connect with the Nasdaq system that reports the prices of recent trades generated a surge of data. That led to a failure of Nasdaq’s backup systems, forcing the market to go offline to fix the problem.
…All told, the data sent greatly exceeded the amount that Nasdaq’s system – known as the Securities Information Processor, or SIP – was intended to handle. People with direct knowledge of the matter said that Nasdaq’s system was not designed to “throttle,” or forcefully slow down, the flood of information. That meant that the data was hitting the SIP at full force.”
Looking back, perhaps it wasn’t a “glitch,” or a software malfunction. Perhaps it was a directed attack on the stock market, using a simple distributed denial-of-service (DDoS) attack that causes an overload of information to a system, forcing it to crash.
Over the past years, stock exchanges all around the world – Australia, Spain, Russia, Japan, New Zealand – have been halted due to “glitches.” Perhaps their systems, too, weren’t a glitch, but a direct attack.
What do you think? Was the NASDAQ failure a glitch? What about the other stock exchanges?
CLICK HERE to Share Your Thoughts
Even European defense organizations, such as governments and media organizations, are being targeted by malware campaigns. Some have even spread to iOS devices.
Via Trendlabs:
“Operation Pawn Storm is an active economic and political cyber-espionage operation that targets a wide range of entities, like the military, governments, defense industries, and the media.
The actors of Pawn Storm tend to first move a lot of pawns in the hopes they come close to their actual, high profile targets. When they finally successfully infect a high profile target, they might decide to move their next pawn forward: advanced espionage malware.
The iOS malware we found is among those advanced malware. We believe the iOS malware gets installed on already compromised systems, and it is very similar to next stage SEDNIT malware we have found for Microsoft Windows’ systems.”
Today, the threat of Stuxnet and other computer and mobile super bugs remain – hidden in the corners of hard drives and other computer devices, quietly waiting for another mission.
It’s no wonder why in recent months, there has been a growing political effort to combat cyber threats. Ironically, its being led by the same group who are thought to be the first movers on cyber warfare.
Cyber War Games
British and US intelligence agencies are about to roll out a transatlantic cyber “war games” to test their resilience against an increasing number of global cyber-attacks.
The first test? A war game against the financial sector.
Via the Guardian:
“The “war game” against the financial sector, which will be carried out in co-operation with the Bank of England and other financial institutions, will be coordinated by a new joint “cyber-cell” that will be established by the two leaders to share information.
Agents from GCHQ and MI5 on the UK side and from the National Security Agency and the FBI on the US side are already working in the US division of the cell. This will be matched by a cyber-cell in the UK.
…The president this week spoke of the “urgent and growing danger” posed by cyber-attacks, which was starkly illustrated by the destructive and intrusive attack on Sony Pictures.
Obama announced earlier this week that he would call for an all-embracing response in his address. In a speech on Tuesday at the National Cybersecurity Communications Integration Center, the president spoke of the need for a “shared mission” involving the government and the private sector. Warning that most of the US’s “critical infrastructure” is owned by the private sector and run on networks connected to the net, the president said: “Neither the government nor the private sector can defend the nation alone. It is going to have to be a shared mission.”
In other words, the threat of a cyber financial attack is very real. That means in order to “protect us,” the government will have to gain even further access to our private and personal data. How will the government do this?
Continued via the Guardian:
“Cameron will also press Obama to put more pressure on the Internet giants, such as Facebook and Twitter, to do more to cooperate with the intelligence agencies as they seek to monitor the communications of terror suspects. The prime minister outlined plans earlier this week to create a stronger legal framework to allow intelligence agencies to break into encrypted communications of suspects.”
It’s no surprise then that Obama just signed an executive order last Friday that encourages and promotes sharing of information on cyber security threats within the private sector. In layman’s terms, it calls for companies to give up information to government agencies.
Major companies such as Apple, Intel, and the Bank of America have already committed themselves to the government’s new cyber threat framework.
That means all of those private pictures, passwords, and documents on your iPhone may not be as private as you may think – and it won’t take a virus for the government to access them.
Is it Necessary?
At the beginning of this letter, I painted a very horrific scenario about how your money – and identity – could be wiped from existence.
That scenario isn’t just a dramatic imaginary depiction of our future.
It is our future. And it’s happening now.
Bitcoin Theft
Over the past year, we have seen millions of dollars worth of Bitcoins lost due to hacks and security breaches.
Last year, one of the largest Bitcoin exchanges lost 850k Bitcoins, worth $500, as a result of hackers.
Just recently, digital currency exchange BTER announced that it has lost 7,170 Bitcoins, or roughly $1.75 million at press time, in an apparent hack on its cold wallet system.
Perhaps Bitcoins are not as safe of an alternative to currency as promoters of it will have you believe.
But neither is currency itself…
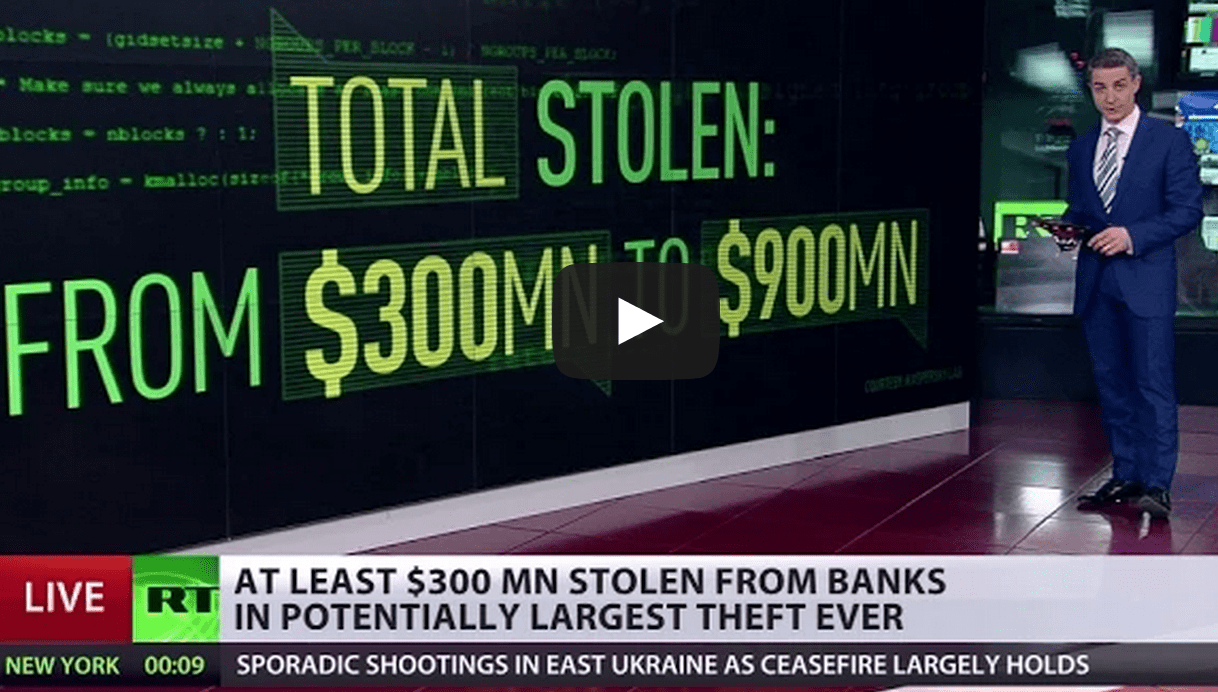
Hackers Steal a Billion Dollars
This past week, Kaspersky reported that up to US$1 billion has been stolen from up to 100 banks:
Via NYTimes:
“In late 2013, an A.T.M. in Kiev started dispensing cash at seemingly random times of day. No one had put in a card or touched a button. Cameras showed that the piles of money had been swept up by customers who appeared lucky to be there at the right moment.
But when a Russian cyber security firm, Kaspersky Lab, was called to Ukraine to investigate, it discovered that the errant machine was the least of the bank’s problems.
The bank’s internal computers, used by employees who process daily transfers and conduct bookkeeping, had been penetrated by malware that allowed cybercriminals to record their every move. The malicious software lurked for months, sending back video feeds and images that told a criminal group – including Russians, Chinese and Europeans – how the bank conducted its daily routines, according to the investigators.
Then the group impersonated bank officers, not only turning on various cash machines, but also transferring millions of dollars from banks in Russia, Japan, Switzerland, the United States and the Netherlands into dummy accounts set up in other countries.
In a report to be published on Monday, and provided in advance to The New York Times, Kaspersky Lab says that the scope of this attack on more than 100 banks and other financial institutions in 30 nations could make it one of the largest bank thefts ever – and one conducted without the usual signs of robbery.”
Some may say it’s a clever ploy by Kaspersky to draw more attention to its cyber security sales. Or perhaps millions of dollars are actually being stolen everyday from our banks without our knowledge.
Is your money safe at the bank?
Is your identity safe with the government?
Perhaps the next market crash will be caused by an act of cyber terrorism.
Be warned.
Be sure to share this with everyone: http://www.equedia.com/worlds-biggest-threat-cyber-warfare
The Equedia Letter












Re: wikispooks.com 9/11 Israel Did It, see latest:
http://www.theeventchronicle.com/study/putin-set-drop-truth-bomb-usa-will-russia-blow-911-wide-open-must-read/
To think that all internet traffic flows over one (public network, like the Trans Canada)Is absurd. There must be at least 4 if not more networks. That hackers( mischievous punks) without high training in computer tech. would be able to execute such destructive missions it must be as real as going to the moon or the ALICE Wonderland story. Such covert operations are the doings of deep pocket political and nationalistic enterprises. the fact of the matter is that war has been humanity’s greatest game since the down of civilization. but using weapons is redundant in today’s world, because with nuclear weapons there is no winner. It has reached the Checkmate point. Thus a new game of poltergeist is invented as who can be like a GOD that knows everything and can do everything our destination is heaven as much as it can be HELL.
What you need is a rolling encryption code. Let me explain.
If I want to download something from you, then I send a onetime
encryption code to you. You take that onetime code and use it to
encrypt the message of information and send it to me. My program
decrpypts the message or information with the same algorithm, and
presto! I have the message or information. Next time- different
code. It’s a bit convoluted but it works.
There is a U.S. company that is, thus far, virtually unknowm that has a procedure for preventing HDD intrusions. Subsequent to a recent meeting that included representatives from Intel, Google, Micron Technology,Samsung ,Lenova,Cisco,Microsoft,IBM et al,a Google and Dell representative joined the Board of Directors of this small company. This company has already produced Self Encrypting Drives and are already being used. Believe that BASF,the major German chemical company has already implemented this approach over a year ago.
You might investigate this and let me know what you learn about The Trusted Computing Group. The name of the company is “WAVE SYSTEMS” (WAVX).
Herb Harris
WAVX, has this ability that you described. Once installed in a corporations computer system,a password is not even required for entry.